Diceware passwords: How to create secure and memorable passphrases

Most people make passwords that are either too weak or too hard to remember. Diceware offers a solution for creating strong passwords that are easier to remember than random character strings, striking a balance between security and practicality.
This guide will explain how Diceware works and examine the practice as a means of illustrating the principles that make passwords strong. Exploring Diceware alongside complementary methods like using an encrypted password manager, it will show you clear steps you can take to improve your overall digital security.
What is a Diceware password?
A Diceware password is a passphrase created by rolling physical dice and referring to a set wordlist (passphrases are passwords made up of multiple individual words). The results are phrases that are much easier to remember than sets of letters and numbers but, if you include enough words, equally hard for threat actors to guess. To give an example, a Diceware password could be “moth uncle syrup banana elder tunnel.”
How Diceware works
Diceware uses everyday six-sided dice to generate random numbers. Each number corresponds to a specific word in a Diceware wordlist. Rolling a die five times (or five dice at once) creates a five-digit number that corresponds to a word on the list. By repeating this process six times, you’ll create a six-word passphrase made of truly random words.
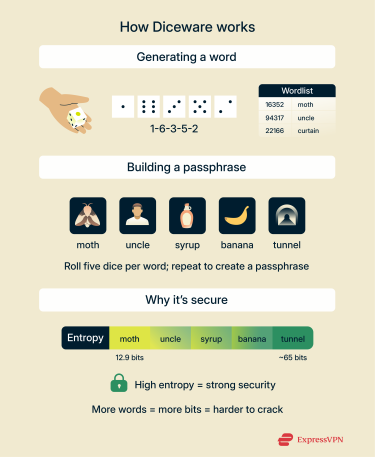
Diceware passwords are strong because when generated correctly, they have high entropy. In this context, password entropy measures how unpredictable a password is. It’s measured in units called bits, with each bit representing a binary choice, like flipping a coin. The more bits of entropy a passphrase has, the more possible combinations an attacker would statistically need to guess it.
Wordlists and randomness explained
At the heart of Diceware is a carefully designed wordlist, where each word is paired with a unique five-digit number. Using a predefined wordlist is important because human beings are not good at exercising true randomness. If you try to invent passphrases yourself, you will often repeat common words or fall into patterns.
The Diceware process removes any personal bias and guarantees true randomness, an essential factor if you want passphrases that are virtually impossible to predict.
Why use Diceware instead of traditional passwords?
Traditional passwords are often based on something familiar: a favorite pet’s name, a popular phrase, or a string of characters altered enough to meet a website’s password rules. While these might seem secure at a glance, they’re usually based on predictable patterns. Cybercriminals know this and build tools that exploit common choices, substitutions, and reused formats.
Diceware takes a different approach by removing human bias from the equation. Rather than count on cleverness or obscurity, Diceware passwords rely on genuine randomness. The result is a passphrase that stands up to both brute-force attacks and targeted guessing. Whether you’re looking to secure a social media account or a crypto wallet, Diceware is a great option.
Memorability vs. security
Strong passwords need high entropy, but purely random character strings are hard to remember. This often leads to dangerous practices like reusing passwords or writing them down in unsecure documents or physical locations.
Using Diceware passwords can help you avoid these issues because it balances memorability and security. For added security and maximum convenience, you can create passwords using Diceware, then use a digital password manager to store and deploy them.
Diceware vs. random character strings
Random character strings like “fG7#kL2!” are strong in theory but impractical in real life. Most people can’t memorize dozens of gibberish passwords, so they either write them down, use them across multiple accounts, or give up and resort to simpler but far less secure passwords.
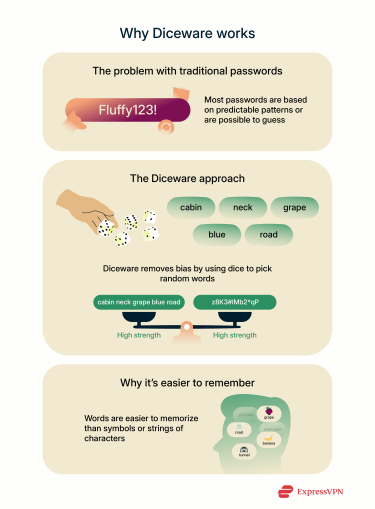
Diceware passphrases like “cabin neck grape floppy flax kingdom road” match or exceed shortish random strings in terms of entropy. For a password cracking program, such a passphrase is even harder to guess than “fG7#kL2!” But for a human, the phrase is significantly easier to type, remember, and deploy across different devices. And since the words are selected randomly, their readability doesn’t reduce security.
The psychology of remembering words
Human memory has not evolved to retain the random strings of letters, numbers, and symbols that typical password generators produce. But it does handle patterns, natural language, and meaning very well. Diceware works with your memory, not against it, by giving you simple words that your brain can recognize, combine, and hold onto more easily.
Even without creating a full story, the natural rhythm and imagery of words help them stick. Whether it’s the sound, the image, or the meaning, each word gives your mind something to associate with. This makes Diceware passphrases more resilient than random characters, even after weeks or months of not using them.
Step-by-step guide: How to generate a Diceware passphrase
Making a secure Diceware passphrase doesn’t require any technical skills or special software. You just need a few physical objects and a bit of time.
Tools you need
To start, you’ll need a Diceware wordlist, one or more six-sided dice, and a way to write down or store the words.
If you don’t have one prepared, you can use our Diceware list. It contains thousands of five-digit numbers, each linked to a word. For maximum privacy, the safest thing to do is download or print the list and use it offline.
Rolling the dice and choosing words
Here’s how to generate each word in your passphrase:
- Roll five dice simultaneously or roll a single die five times.
- Record the result of each roll in the sequence to form a five-digit number (for example, 34621).
- Look up that number in your wordlist and write down the associated word.
- Repeat this process for as many words as you want in your passphrase.
Tip: After generating your new passphrase, store it in a password manager secured by a strong master password and zero-knowledge encryption. Avoid leaving the paper copy lying around, and never write the passphrase down in a note app, text document, or any unsecured file.
How many words do you need?
Five words is the absolute minimum we can recommend. But if you’re securing something more sensitive, like encrypted backups, financial data, or administrator-level credentials, go with six or more words.
Each additional word adds entropy, which exponentially increases the time and computing power needed to guess the full passphrase. Because it’s made up of whole, readable words, not gibberish, just adding a word or two doesn’t make it much harder to remember. For a better sense of how passphrase length affects security, check out these example passphrases.
It’s best to separate each word with a standard character. You could use a space, but many accounts require passwords that include numbers and special characters. For that reason, you may want to alternate putting a symbol and a number between words. It’s best to keep to a standard pattern to prevent forgetting your password.
Diceware + password manager + 2FA = strongest setup
Diceware passphrases are usually much more secure than typical passwords, but you can improve your protection even further. Combining a Diceware passphrase with a password manager and two-factor authentication (2FA) is an easy way to boost your digital security. Each tool provides a different layer of defense, covering weaknesses in the others. If you’re new to 2FA or want a refresher, here’s a thorough guide.

How do they work together?
Each tool in this setup plays a distinct role in strengthening your security.
- Diceware passphrase: Gives you high-entropy passphrases that are strong by design, not just complex on the surface.
- A password manager: Stores your passphrases and other credentials in an encrypted vault that syncs across devices. This means that you don’t have to memorize anything beyond your master password (or master passphrase).
- Two-factor authentication (2FA): Adds a final layer by requiring a second action, like entering a time-based code or tapping a physical security key, before access is granted.
This combination means that even if someone obtains your Diceware passphrase through a phishing scam or data breach, they still can’t get into your account. It also helps you avoid weak or reused passwords, since your password manager handles that for you and solves the memorization issue.
Many password managers include quality-of-life features like autosave/autofill alongside security tools that monitor for weak, breached, and reused passwords. Some options, like ExpressVPN Keys, also come with 2FA code generators and a bundled VPN.
Minimizing risk with layered security
Modern cybersecurity practices typically revolve around layering. The idea is that if one layer fails, the others will still protect your accounts. Diceware, password managers, and 2FA each reduce a different kind of risk:
- Diceware reduces the chance of your password being guessed or cracked.
- Password managers reduce the risk of password reuse, weak credentials, or storing logins in unsecured locations.
- 2FA protects against stolen credentials being used by anyone who doesn’t have access to your second authentication factor.
Together, they shrink your attack surface significantly. Even if a device is stolen, a site is hacked, or you get phished, your most important accounts remain protected.
Common mistakes to avoid when using Diceware
While Diceware is a simple and powerful way to create secure passphrases, its effectiveness depends on how you use it. Here are some of the most common missteps that can quietly weaken your security, and how to avoid them.
Reusing the same words
One of the most common mistakes is picking words yourself instead of rolling the dice. Choosing memorable or everyday words like “apple,” “dragon,” or “blue” often happens instinctively, but it’s not ideal for security. Human memory tends to make us repeat familiar or emotionally loaded choices, which often appear in password leaks and attacker wordlists.
Take a password like “Sunshine2022!” It has a decent length and includes numbers and symbols, but it’s based on a popular word and a predictable structure. Attackers account for these patterns with tools designed to combine dictionary words, years, and common substitutions. What looks secure on the surface can be guessed quickly in practice. Diceware avoids this by replacing personal bias with true randomness.
Using too few words
Short passphrases are easier to remember and use, but they provide much less protection. Each Diceware word adds about 12.9 bits of entropy. The more words you use, the stronger your passphrase becomes.
| Passphrase length | Entropy (approx.) | Security level |
| 3 words | ~39 bits | Weak; crackable with modern tools |
| 4 words | ~52 bits | Borderline; acceptable only for low-risk use |
| 5 words | ~65 bits | Acceptable; works for relatively unimportant accounts |
| 6 words | ~77 bits | Strong protection in most personal settings |
| 7+ words | 90+ bits | Excellent for long-term or high-risk protection |
A passphrase made up of three or four words might feel secure because the words are random, but the fundamental math is still fairly weak. To resist brute-force cracking, aim for at least six words, especially if the passphrase protects a sensitive or otherwise important account.
Mixing languages or adding predictable modifiers
It might be tempting to “enhance” a Diceware passphrase by adding symbols, numbers, or switching languages. For example, turning “sand grand trail” into S@ndGr4ndTr@il!. While this may look more secure at a glance, the complexity is somewhat superficial. When people are tasked with creating complex passwords using symbols and letters, they generally fall into predictable patterns, like swapping “a” for “@” or capitalizing the first letter.
Password-cracking tools often account for these common practices. They don’t just try to guess words but also apply rules for common modifications, including leetspeak (replacing letters with numbers or symbols), capitalization, and added punctuation. These tweaks introduce structure into what should be random, making your passphrase easier to crack.
Even mixing in foreign words or phrases can backfire. Chances are, any second-language words you’d be tempted to include reflect your life experience or background. If you’re being specifically targeted, your attacker may know these things. This is also why using numbers tied to personal identifiers like your address or birth year is a bad idea.
Stick to an established database and select words as dictated by the dice. Doing so is the best way to ensure your passwords are truly random.
Overlooking length limits
Some websites impose maximum character limits on passwords, sometimes as low as 16 or 20 characters. Since Diceware passphrases often contain multiple words with spaces, they can easily exceed these limits.
If you're restricted by length, you can opt to only use the first few letters of each word. Alternatively, use randomly generated keys from a password generator like the one included with ExpressVPN Keys. It’s highly customizable, letting you set password length and rules for the inclusion of special characters.
FAQ: Common questions about Diceware passwords
How do I reset my Dice password?
Resetting a Diceware password isn’t too different from resetting a normal password. Use the account’s password reset method to confirm your identity. Then, when asked to create a new password, bring out your dice and wordlist. To avoid needing to reset in the future, consider storing your Diceware passphrase in a secure password manager like ExpressVPN Keys.
How long should a Diceware passphrase be?
In most cases, a Diceware passphrase should be at least six words long. This gives you around 77 bits of entropy, which is strong enough to resist modern brute-force attacks. For higher-risk or long-term protection, aim for seven or more words. Fewer than five words is not recommended, as it significantly lowers your security.
What should I do if I lose my Diceware passphrase?
If you lose your Diceware passphrase, you may need to reset it. The process of doing so varies depending on the account it was tied to. In any case, generate a new one immediately and update it in the associated account. There’s no way to recover a lost Diceware phrase unless you backed it up securely in a password manager like ExpressVPN Keys.
What’s the difference between a passphrase and a password?
A passphrase is typically longer and made of multiple real words, while a password is often shorter and may include random characters. Passphrases like “peanut gown ore home curtain spoon” are easier to remember and can offer more security due to higher entropy. Passwords like “fG7#kL2!” are complex but are harder to recall and often reused.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN



















Comments
I'm completely flummoxed... no surprise there given my inexperience. However, I can't even yet determine if I even have an account or not. Pathetic, I realize, but I suffer short term memory loss. I can't recall if I finalized payment. Please, if anyone can help, I'd appreciate it immensely.
Hi Leslie. Please contact our Support Team. They will help you.
Holy f#cking wow honestly I'm fully mind blown on who theee super human is who wrote this deadset I'll be in touch if I need help I'm too stressed to put 2 and 2 to get her... Thanks so very much people wow just wow.